The convergence of Information Technology (IT) and Operational Technology (OT) continues to transform the industrial landscape, bringing with it a new complex array of cybersecurity challenges.
As a cybersecurity professional, I am deeply engaged in addressing these challenges, particularly the critical aspect of secure remote access in environments involving Industrial IoT and OEM equipment. This blog explores the essential role of Zero Trust security models, emphasizing the innovative approach of Invisinet in this domain.
Challenges in Secure Remote Access
Traditional approaches like truck-rolls for onsite OEM equipment maintenance are increasingly replaced by remote access methods for efficiency. However, this shift introduces notable cybersecurity risks. In an IT/OT converged environment, network-connected devices, once remotely accessible, become potential targets for cyber-attacks. The stakes are high in OT systems, where breaches can lead to severe operational disruptions and safety hazards.
Limitations of Conventional Security Measures
Conventional security measures, including credential-based access and Multi-Factor Authentication (MFA), are proving inadequate in the integrated IT/OT landscape. These methods, while basic, do not fully address the sophisticated nature of modern cyber threats. Practices like opening firewall ports for remote access bring inherent risks and vulnerabilities, including human error and potential unauthorized access.
Introducing Invisinet: A Zero Trust Approach
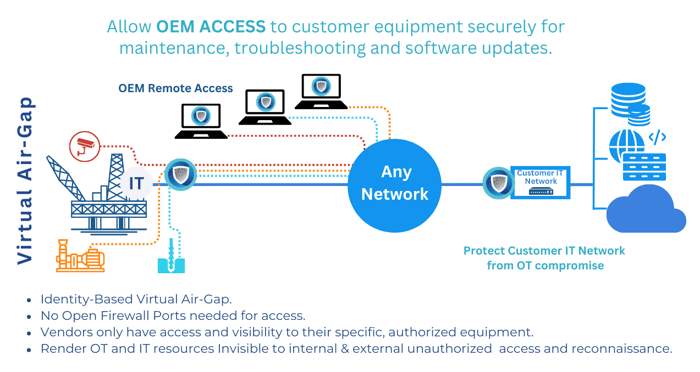
Invisinet's solution is grounded in the Zero Trust security model, which operates on a 'never trust, always verify' principle. This approach is particularly effective in IT/OT environments. Invisinet features include:
- A Virtual Air-Gap: Eliminating the need to open firewall ports, Invisinet enhances security by controlling access based on verified identity.
- Identity-Based Micro Segmentation: Invisinet enforces identity at the network session setup, ensuring that maintenance personnel access only their designated equipment, thereby preventing unauthorized network access.
- Granular Audit Trail: Offering detailed records of network interactions, Invisinet enhances operational transparency and simplifies access management.
Implementing Zero Trust in IT/OT Environments
Adopting Zero Trust in converged IT/OT systems involves robust identity verification mechanisms. Assigning identities to each device and client ensures authenticated and authorized access, moving beyond traditional perimeter-based security models to address the complexities of modern interconnected systems.
Call to Action
For organizations prioritizing the security of network access in OEM environments, or OEM vendors dedicated to ensuring customer confidence, we invite you to connect with us. Our team is ready to provide detailed insights into Invisinet’s robust security solutions, demonstrate its straightforward implementation process, and explore the diverse applications of identity-based access and micro-segmentation in enhancing your cybersecurity posture. Contact us today to learn how we can collaboratively elevate your network security strategy.
Conclusion
The integration of IT and OT systems necessitates a new approach to security. Adopting a Zero Trust model, particularly through solutions like Invisinet, is vital in this new era. For organizations concerned with network security in supply chain or OEM equipment management, embracing an identity-based Zero Trust approach is crucial. Invisinet exemplifies an effective implementation of this model, providing robust security against evolving cyber threats. Reach out to explore how Invisinet can enhance your secure remote access strategies in today’s interconnected world.

