The Securities and Exchange Commission (SEC) recently enacted new cybersecurity rules that require public companies to disclose material cybersecurity incidents within four days and provide material information on their cybersecurity risk management, strategy, and governance on an annual basis. These rules are designed to provide investors with greater transparency into the cybersecurity risks facing public companies and to help them make informed investment decisions.
The new rules are particularly important for companies with operational technology (OT) environments. OT systems are used to control critical infrastructure, such as power plants, manufacturing facilities, and transportation systems.
Prioritize Operational Technology Security Posture
Operational technology (OT) refers to the systems and networks used to control and monitor physical processes in industries such as manufacturing, energy, and transportation. These systems play a critical role in the functioning of essential infrastructure, making them attractive targets for cyberattacks. A cyberattack on an OT system could have a devastating impact on the company's operations and could also pose a risk to public safety.
Attacks are increasing in frequency and severity. According to a report by the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), the number of reported cyber incidents targeting industrial control systems (ICS) has increased by more than 200% in the past five years. And, the severity of these attacks is also increasing, with more and more attacks causing physical damage and disruption to operations. In 2022, there was a 140% increase in cyberattacks against industrial operations, resulting in more than 150 incidents*.In light of this, OT security should be prioritized to ensure the protection of these critical systems.
Proactive Practices for Compliance
SEC regulations outline specific requirements that organizations must adhere to in order to ensure the security and integrity of their organizations inclusive of their OT environments. These requirements include:
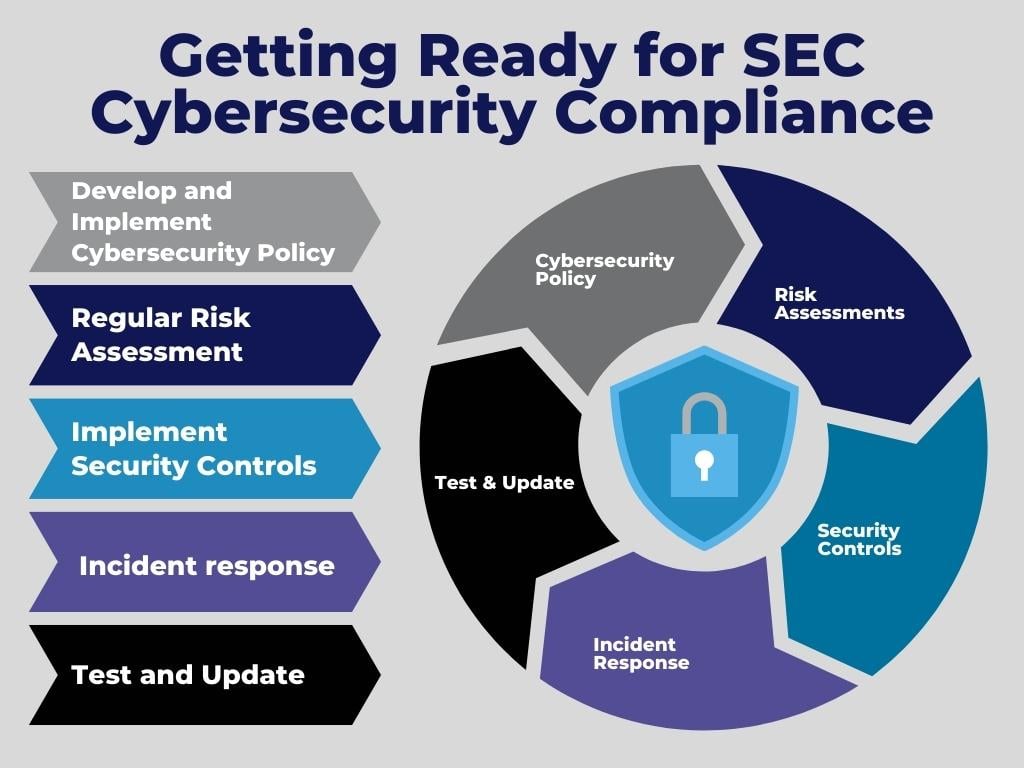
- Develop and implement a cybersecurity policy. This policy should outline the organization's cybersecurity policies, and procedures, and set expectations for employees.
- Conduct regular risk assessments. This will help the organization to identify and mitigate cybersecurity risks.
- Implement security controls. This includes controls such as firewalls, intrusion detection systems, and access control lists.
- Monitor and respond to cybersecurity incidents. The organization should have a process in place for detecting, investigating, and responding to cybersecurity incidents.
- Test and update the cybersecurity program regularly. The organization should test its cybersecurity program regularly and make updates as needed to maintain compliance.
Reduce Risk with Invisinet
Invisinet: The Zero Trust Cybersecurity Solution
Cyberattacks are a growing threat to critical infrastructure, all publicly traded organizations in the regulated sector are required to comply with SEC cybersecurity regulations. Invisinet is a Zero Trust cybersecurity solution that can help such organizations with compliance and cyberattack prevention solution.
Invisinet's solution is simple, effective, and goes beyond Zero Trust by enforcing identity-based controls at the network layer and micro-segmenting the network to isolate, conceal, and safeguard critical assets.
- Enforce identity-based access control: Invisinet ensures that only authorized users can access critical applications, devices, and infrastructure.
- Micro-segment the network: Invisinet isolates critical assets from each other and from the rest of the network, making it more difficult for attackers to move laterally and compromise network assets and data.
- Cloak network assets: Invisinet conceals network assets from unauthorized traffic, making it more difficult for attackers to even see the assets they are trying to attack.
* Waterfall Security
